Best AI-Driven,
End-to-End Cybersecurity Solutions for Your Business
Utilize machine learning to automatically detect cyber-attacks.
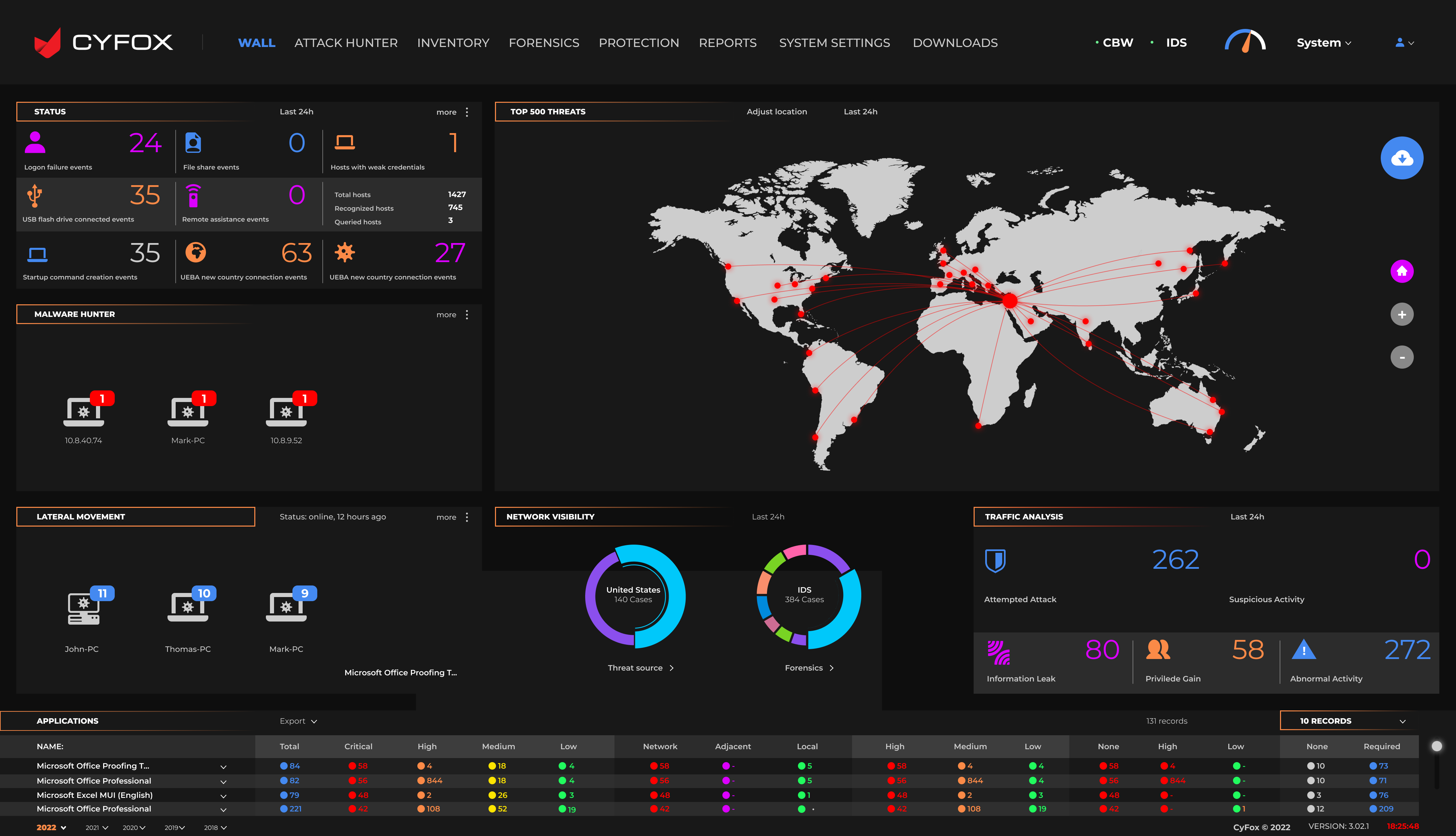








































































EDR, XDR/SIEM, SOCaaS
CYFOX's all-in-one cybersecurity suite, encompassing EDR, XDR , and SOCaaS, offers a robust, multi-layered defense mechanism for your businesses. This comprehensive approach ensures seamless integration and coordination across different security layers, providing enhanced threat detection, faster response times, and streamlined incident management. By consolidating these critical services into one cohesive package, CYFOX not only simplifies the cybersecurity management for businesses but also offers a cost-effective solution that eliminates the need to invest in multiple standalone security products. This integration results in improved overall security posture, making it an ideal choice for businesses seeking efficient and effective cybersecurity solutions.
Next-Gen multi layer AI attack hunting
CYFOX's Next-Gen Multi-Layer AI Attack Hunting employs layered AI algorithms to create a formidable defense against cyber threats. This advanced system integrates multiple AI-driven analytical layers, enhancing the detection of complex, multi-stage attacks. By correlating diverse data points and employing predictive analytics, it proactively identifies and mitigates emerging threats, ensuring superior protection for businesses in the ever-evolving digital landscape.
The AI advantage
Better. Faster. Stronger.
Leveraging the power of AI, CYFOX delivers superior cybersecurity: more robust, faster in threat detection, and stronger in defense capabilities.
Adapt to new attacks
CYFOX's AI-driven cybersecurity adapts swiftly and intelligently to emerging and evolving cyber threats.
Reduces workload
CYFOX's AI technology streamlines cybersecurity operations, significantly reducing the workload for IT teams.
More features
CYFOX Cloud
CYFOX Cloud's architecture, rooted in its multi-tenant, multi-vendor, multi-region capabilities and integrated with AWS technologies, offers a comprehensive and secure solution for XDR/SIEM, billing, and licensing management. This platform is tailored for diverse users, ensuring compliance with data protection laws like GDPR and providing a scalable, efficient, and secure cloud-based environment for cybersecurity operations.
CYFOX EDR - AG.AI
The multi-layered AI approach in the EDR system, supplemented with traditional signature scanning,provides a comprehensive defence strategy. It enhances the ability to detect and respond to a variety of cyber threats, from conventional malware to sophisticated, evolving attacks. The architecture focuses on proactive threat detection, adaptive defences, and thorough threat hunting, ensuring a robust and resilient endpoint security posture.
IDS Engine
The IDS solution uses port mirroring to provide a powerful, non-intrusive way to monitor network traffic, ensuring thorough security surveillance while maintaining network performance. This flexible approach can be tailored to specific network segments, making it a valuable tool in the cybersecurity arsenal.
Weak Passwords Engine
Penetration testing for weak passwords, especially when using VLAN tagging to access different network segments, is a thorough and effective method to uncover security flaws related to password management. This comprehensive approach not only identifies existing vulnerabilities but also guides the strengthening of security protocols, leading to an enhanced defence against potential cyber threats.
Vulnerability Engine
Our AI-powered vulnerability engine represents a sophisticated and comprehensive approach to vulnerability management. By integrating diverse data sources, employing advanced AI for analysis, and providing actionable insights, it significantly enhances our ability to identify, prioritize, and report on vulnerabilities across a complex and diverse digital environment.
NAC Engine
Integrating SNMP with a NAC system to control network access effectively combines network management protocols with security policies, resulting in an automated, efficient, and secure approach to managing network access. Our implementation enhances the ability to safeguard the network against unauthorized devices, thereby bolstering overall network security and compliance.
CYFOX Event Manager
The integration of Syslog messages with CYFOX Cloud/SIEM is a pivotal element in enhancing network security management. It offers a centralized solution for advanced analysis, threat detection, and compliance management. This approach is integral to a comprehensive cybersecurity strategy, ensuring vigilant monitoring and proactive response to potential security threats.
FIM Engine
CYFOX FIM system is a valuable tool in cybersecurity, providing real-time monitoring and alerting for file integrity. It plays a crucial role in detecting and responding to malicious activities, thereby enhancing the security of sensitive data and system configurations. This system is not only important for proactive threat detection but also for compliance and forensic purposes, making it an integral component of modern cybersecurity frameworks.
Overcome your cybersecurity operational hurdles effectively
Simple Implementation
Experience swift and flexible deployment tailored to your needs, with options for non-intrusive agentless, robust agent-based, or a hybrid approach, all achievable within just a few hours.
Improve SecOps
Enhance your cybersecurity with CYFOX's expert SOC service, offering continuous monitoring, tailored threat intelligence, and rapid incident response for robust, round-the-clock protection.
Maximize Efficiency
Enhance continuous cyber defenses, providing accurate insights across all organizational levels.
One Managed Solution
CYFOX unifies cybersecurity tools for a comprehensive defense on a single platform.
Flexible Deployment
Choose between on-premise deployment, cloud, or as an MSSP managed service.
Less is more
Less Expense, More Value
Experience a cost-effective, end-to-end solution with 10 integrated, comprehensive engines in a single, user-friendly package.
Less Complexity, More Impact
Our autonomous, all-in-one security platform simplifies integration and management, reducing the need for multiple solutions and extensive staffing.
Less False Positives, More Precision
Elevate your detection and response capabilities with our refined approach, minimizing distractions and maximizing security effectiveness





.svg)







